The current era remains excessively dominated by data, information, and technology. Today, businesses and researchers are busy harnessing the absolute power of Artificial Intelligence and all that it offers. With Generative AI in the picture, the potential keeps rising, ensuring a new dawn for businesses.
AWS GenAI in particular has revolutionized different industries by generating and mimicking human-like texts, images, and codes. But let’s not forget that “with great power comes great responsibility.” Therefore, trusted and recognized service providers like AWS remain top of the list in privacy policy and management.
As you embark on your journey to scale Generative AI models on AWS, it’s vital to make sure that data privacy is at the forefront of each strategy. Today, through this blog, we are going to delve into the best practices for data security while securely scaling GenAI models on AWS.
Best Practices for Data Security and Privacy
Today, data is the lifeblood of organizations, driving innovation and efficiency. But as the volume and the value of the data continue to increase, the importance of data security and safeguarding it intensifies. The stakes are already high, and with data breaches, privacy violations, and data theft, catastrophic financial losses keep looming over the heads of the organizations.
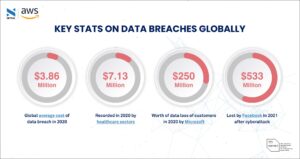
Did you know that IBM revealed it takes an average of 280 days to identify and contain a data breach?
Hence, it’s imperative to adopt and adhere to the best practices for data security and privacy, protecting sensitive information, staying compliant with regulations, and maintaining trust of the customers. Let’s look into best practices for data security in this digital age!

Start with Robust Data Privacy Strategy
Before delving into the technical aspects, it is crucial to establish a strong data privacy strategy. First, gain a deep understanding of the data you are working with. Next, identify any possible privacy risks and develop policies and guidelines to reduce these risks. Ensure team training on data security practices, including the understanding of the importance of data privacy.
Use AWS Identity and Access Management (IAM)
Do you, Amazon Web Services Identify and Access Management, serve as your primary safeguard against unauthorized access? You can assign precise permissions to people or services by restricting access to only the essential tasks required for their respective roles. It is important to regularly review and audit these permissions to ensure they remain in line with your evolving security needs.
Employ Data Encryption
Data encryption at rest and in transit is a necessity in any security-conscious information management system. Amazon Web Services (AWS) offers a wide range of services, such as Amazon S3 and Amazon RDS, which provide encryption as a default feature.
These services are for securely storing and transmitting sensitive data while ensuring data remains protected from unauthorized access throughout its lifecycle. It is vital to utilize these services to guarantee data confidentiality and integrity and to meet compliance requirements.
Implement Network Security and Solid VPCs
Amazon Virtual Private Cloud (VPC) provides a reliable platform to create secure and isolated network environments. You can establish a secure network that protects sensitive information from unauthorized access by segmenting your AWS GenAI model infrastructure, data storage, databases, and other resources.
The VPC platform enables you to configure security groups and network ACLs allowing you to monitor and control traffic flow while ensuring the network remains secure. By implementing these measures, you can safeguard your sensitive data and minimize the risk of security breaches.
Secure Your Data Storage
It’s another crucial database security and privacy best practice! When working on GENAI models, the storage of massive datasets is often a requisite. It is vital to establish access controls and data classification mechanisms to ensure that exclusively authorized personnel can access sensitive data. Data access can be effectively managed by leveraging Amazon S3 bucket policies and object-level permissions.
Data Anonymization and Minimization
When preparing data utilization in conjunction with the GenAI model, it is essential to consider techniques that minimize and anonymize data. Personal Identifiable Information (PII) should be removed or de-identified to reduce privacy risks. Impact on individual privacy can be minimized, in case of model compromise through this step.
Data minimization techniques aim to reduce the amount of data collected, processed, and stored. On the other hand, anonymization techniques aim to make it impossible to identify individuals from the data. Both techniques are essential to ensure that the privacy of individuals is protected while still benefiting from the use of AI.
Ensuring Security Through Timely and Consistent Updates
It is imperative to ensure the maintenance of your AWS GenAI infrastructure with the latest security updates and patches. To achieve this, AWS provides managed services, such as Amazon EC2 Systems Manager, that offer automation of the process. It effectively reduces the risk of vulnerabilities and data theft. It also guarantees that your infrastructure remains secure and functional while eliminating the possibility of exposure to malicious attacks. It is a crucial aspect of the IT security best practices checklist!
Continuous Audit and Monitoring
To ensure the security of your infrastructure, it is crucial to implement comprehensive monitoring and auditing solutions. AWS offers effective services such as Amazon CloudWatch and AWS CloudTrail that help you track and log activities, detect potential security threats, and respond to them quickly. Amazon CloudWatch enables you to monitor resources and applications in real time and automatically triggers alerts if it detects any abnormal behavior or performance issues.
AWS CloudTrail provides a detailed record of all API calls and events, allowing you to identify the source of a security incident and take necessary measures to prevent it from happening again. By leveraging these monitoring and auditing solutions, you can improve your security posture and protect your infrastructure from potential threats.
Train Your Team
It’s essential to understand that your security is only as strong as its weakest link. To ensure data privacy, follow data security best practices, such as investing in ongoing security training for all your team members. Through this, everyone will know their role in safeguarding information. You should conduct regular security drills and incident response exercises to test your preparedness and ensure your team is always ready to handle any security threats.
Maintaining Compliance and Regulation
It’s essential to stay abreast of data privacy regulations that impact GENAI projects, such as GDPR, HIPAA, or CCPA. Fortunately, AWS offers compliance documentation and services to assist with alignment with these regulations. By utilizing these resources, organizations can ensure their adherence to data privacy requirements and foster trust with customers.
Secure and Confidently Scale Your Generative AI Models with AWS
As artificial intelligence continues to transform industries, protecting sensitive data has become a top priority. By implementing industry-leading best practices for data security, you can confidently scale your GenAI models on AWS while maintaining a steadfast commitment to data privacy.
It’s crucial to recognize that safeguarding data privacy is not a one-time effort but an ongoing obligation. As the landscape of threats continues to evolve, it’s critical to remain vigilant and adapt accordingly. By doing so, you can ensure that both your organization and your users are protected in the age of artificial intelligence.
Are you looking for a reliable GenAI and AWS partner to assist you in embracing the new technology in the most effective way? Contact NETSOL today and schedule a meeting with our representative. It’s time to explore and assess your data privacy for any loopholes. It’s time to stay vigilant and alert! Start your journey to a safe data environment with AWS!



Leave a Reply